Webauthn User Verification
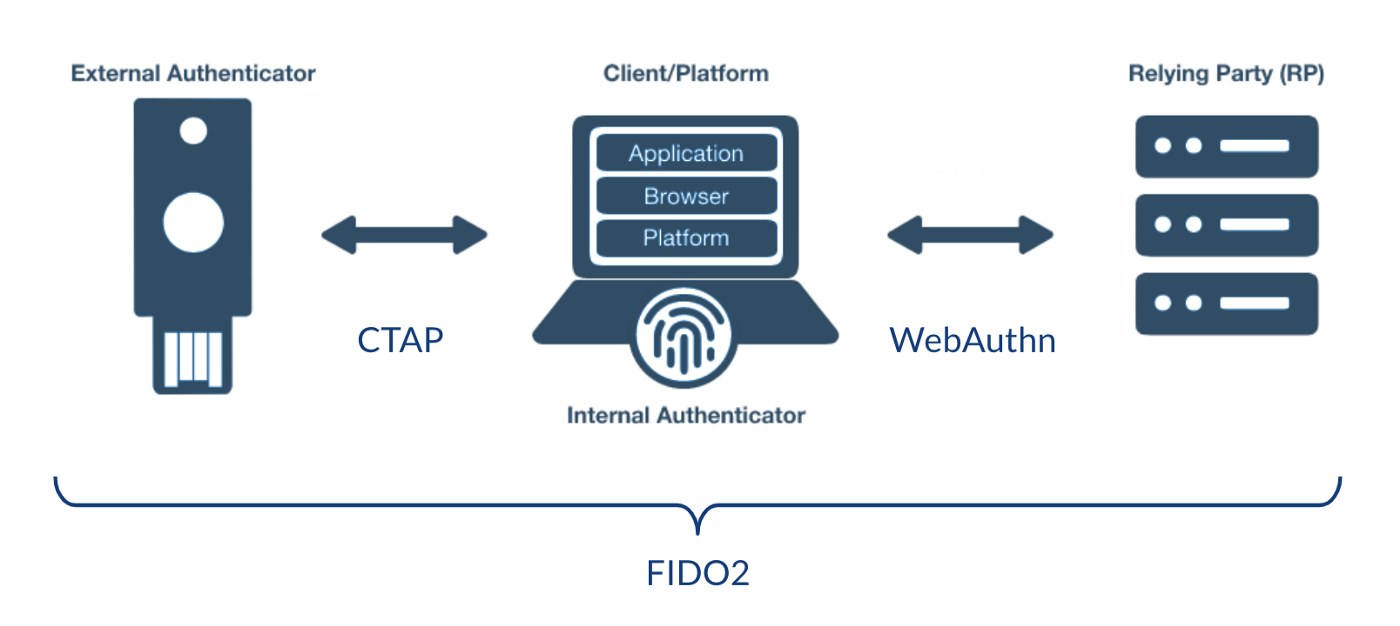
WebAuthn allows authentication through FIDO 2 ("InternetAuth / WebAuth"). It supports 2 authentication methods: FIDO2 WebAuth follows FIDO 2 Web Authentication standards. Once Authenticators has been enabled the end user will be able to choose this option during registration to use for further authentication. Configure your YubiKey OTP for single-time password mode.
This article describes procedures that the Servers will be required to perform to validate WebAuth responses. If you are looking for a good introduction to the WebAuthn APIs, you should read the article below. Your employees will never be able to access a computer. Their data will go missing. They don't even know about meetings.
The authentication flow looks similar to the registration flow. The primary differences are: Authentication does not require user information Authentication creates an assertion signed by the previously generated private key that is associated with the relying party rather than signing with the attestation certificate.
Unable to implement Authenticator Policy
However, one of the major problems with Webauthn is its ability to support User Verification, because user verification is based upon requesting/responding based on devices and there is no device attribute in this context. Imagine if an iPhone or laptop is enrolled using U2F + password or iPad Touch ID. Both have multiple multifactor credentials. The U2F is an integrated single-factor device that becomes multiple-factor when combined with passwords. In its own right it can have multiple factor authentication and biometric verification. We should be able to have a website request processed and based on the device used we can flow.
The RP directs the authenticator to perform user verification, the authenticator performs user verification locally and signals to the RP whether user verification was successful. User verification can take various forms, such as password, PIN, fingerprint, public key credential, etc.
End-user experience
When the authentication option is selected at login the user is allowed to use that as a second authentication. In varying situations end users may require e-mail verification. Alternatively, this verification may include biometric challenges, PINs and passwords, as well as tapping the devices. When you register a WebAuthn Security Key or Biometric authenticator, you must provide Okta with information on who is requesting authentication. FIDO2 is a WebAuthn authentication tool allowing FIDO to be listed by user name in the Extra Verification section on your Settings page.
User presence
Use Cases The use of User Presence or User Verification depends on the specific use case: User presence is appropriate for second factor authentication (2FA). User verification is not recommended for 2FA because the user will have already entered a shared secret (password) sent to the server over the network.
Passkey management
FIDO 2 FIDO credential is used for the authentication of multiple mobile devices including tablets or notebook computers. This credential can be shared on multiple OS platforms. Using passcodes WebAuthn can save data on multiple devices for backup or synchronization. It preserves WebAuthn/FIDO's strong keyless/nonphishingable authentication model while offering enterprise-level security features. This is a feature that is currently only available through some WebAuthn authentication systems. The security of the user's device does not require carrying a key.
Allow the use of passkeys
This default settings are set. Turn off this option and allow the use of passkeys in the organization. In the Administration console, navigate to > Features > Configuration.
Block the use of passkeys
The feature will defaultly be removed. Turn on the pass key and block it from running: On the Admin console, click Options > Features.
Some background on Webauthn
We should learn the Webauthn history first. Webauthn is a standard enabling a client to authenticate with a website using cryptographic authentication. Webauthn describes how cryptographic authenticators can communicate between clients. Examples of authentication devices include U2F tokens (yubikeys), TouchIDs on Android, iOS and iPad, and Trustable Platform Modules on Windows Hello. Webauth has to account for differences in these hardware classes and how they communicate, but ultimately each device performs a set of tasks.
Attested credential data
Bits 0 and 2 are User Presence and User Verification flags. Bit 6 is AT(Attested Credential Data). Must be set when attested Credential Data is presented. Bit 7 must be set if extension data is presented. Counter 4byte counter.
An entry includes the type of the credential and credential id, and optionally a list of transports the client can use to find the credential. challenge: contains a random value generated by the RP from the authenticator to sign as part of the authentication assertion. Relying party identifier claimed by the caller. This must exactly match the specified during registration. timeout: the time, in milliseconds, that the caller is willing to wait for the call to complete.
The authenticator data is a byte array containing data about the get credential operation, including a signature counter and a hash of the RP ID. flags: The AT indicates whether the authenticator added attested credential data, and is always 0 in assertions. The ED flag indicates if the authenticator data has extensions. The UP flag indicates if the user is present. The UV flag indicates if the user is verified (PIN or Biometric).
Is WebAuthn secure?
WebAuthor has been designed as an authentication system which allows a user to use the same credentials for multiple users. It's phished resistant and mainly stores public data only in a database with most private information usually only in hardware authentication.
How To Sign a Document Electronically Create an electronic signature: Depending on the document, you may use a digital signature, a scanned image of your handwritten signature, or a software-generated image of your name.
Webauthn. User verification policies. Curiosities
Recently I was notified of two interesting bugs that Webauthn's authentication would not run with Firefox and Chromium. These were a bug in Webauthn. It was confusing and didn't happen to me. I also bought one of the devices I was using and waited a month for the Australian Post to lose this one. In addition to switching browsers I started using a browser called Edge and started to notice strange behaviour - the login prompted my password.
The same should be done for credential validation where userVerification is currently unspecified and defaults to preferred . In that case it would just be to streamline the demo; I'm not aware of any problems caused by the default value.
OTP verification (one-time password)
OTP Verification is a process of verifying the identity of a user by validating an OTP (one-time password) sent to the user's mobile phone or email address. This process is used to ensure that the person attempting to access an account or service is the legitimate owner of that.
What is Customer Identity Verification?
You can define Customer Identity Verification as the process of cross-checking a customer’s personal identification details with new and existing records to establish proof of identity and prevent fraud, often using digital technologies like video-based verification, biometrics, digital signatures, and the like.
Preferred becomes Discouraged
This creates a risk that since Preferred - tests the verification but cannot be found - the U2F device can now be “downgraded”. The server could also tamper and remove user verification parameters silently if the client has the same request. In reality, Preferred policy is similar to Discouraged, but with an annoying UI/UI for people who must verify their identity without any real information about the user being verified.
Devices change behaviour
This means during registration he can request the policy (which will be required), however the policy cannot be used later in the process. Another type of behavior changes happen when devices used by Chrome require preferred user validation. The requirement allows sites to have hardware that isn't compatible with any other browser. The change in behavior can confuse the user.